Even the simplest of design projects requires a multitude of stakeholders to ensure its success, all of whom need access to your design data so they can do their jobs effectively. However, dishing out CAD files like candy is not the best approach for a number of reasons. In short, the wrong data falling into the wrong hands can be extremely damaging to your business.
There are two main reasons why storing design data in files is a bad idea. The first is that CAD files store a snapshot of your data at the moment in time the file was copied. Actually, that’s the second reason, too. Copying and distributing files is the root of all data disasters, whether your manufacturing partner is machining out-of-date parts or your competition can’t believe they were emailed your files by mistake.
Files make keeping track of who has access to your intellectual property impossible. Once files have been copied and sent by email, they are completely out of your control. You can mitigate this to a certain extent by putting a more formalized process in place to manage who has access to your data, such as a PDM system. However, PDM systems just add an extra layer of complexity that slows everyone and everything down, stifles creativity and doesn’t really solve the problem.
As long as people are able to make copies of your design data on their computers, you’re at risk of costly manufacturing errors and IP security issues. PDM systems do provide some level of control, but the costs of setting up and maintaining the required IT infrastructure can be prohibitive (probably the reason why most companies don’t use them).
Onshape, on the other hand, has all the data management tools you need built in and anyone with the right permissions has instant access to the latest, up-to-date design data. This data can be shared securely with coworkers and external vendors alike, giving you full control over who can do what with your valuable IP.
While this level of security and access control is more than sufficient for most, Onshape Enterprise takes security and control even further. Role-Based Access Control (RBAC), comprehensive audit logs, centralized access reports and enforced 2-Factor Authentication (2FA) ensure that your data is safeguarded with the highest possible level of security at all times. Let’s take a look at these features in more detail.
Role-Based Access Control
Access permission types are identical for all editions of Onshape: View, Comment, Export, Edit, Link, Share and Copy. Using a combination of these permissions enables you to precisely control which actions each user or team of users can take with your data. These permissions are set each time a new Document or Folder is shared with a named user or a predefined team of users. That’s all well and fine, but it can become repetitive and subject to mistakes. Also, keeping track of who has access to your data may become unmanageable if you have lots of it.
Role-Based Access Control in Onshape Enterprise enables companies to configure multiple roles and permission schemes and apply them to a Project. While an Onshape Document can in itself be a project-level container (i.e., it can contain all the parts, assemblies, drawings, PDFs, etc. that make up a project), in reality project data is usually distributed amongst multiple Documents. To ensure that the correct security permissions are applied to an entire project, Onshape Enterprise introduces a new type of object called a “Project.” This is a unique type of top-level Folder that can be used to manage and control all your data using roles and permission schemes.
A role can be better described as a job function: designer, manager, contractor, etc. A role is really just a convenient way to describe a particular job function a person or team will perform during the lifetime of a project. A permission scheme then sets up what each of those roles is able to do to give them the precise privileges that are appropriate to their current assignments. For example, a person working on one project may be required to edit designs, but on another, only to review them. So rather than having to remember the permissions that a reviewer should have, you can define a role called “Reviewer” and a permission scheme that gives a reviewer “View and Comment” permissions. These schemes and roles are then defined at the Project level and all Documents within that project will inherit those permissions.
Project dialog showing permission schemes and access roles
Configurable permission schemes and role-based access ensure that security measures for each project remain in line with your company’s policies, prevent mistakes and reduce repetition to ensure that your company data can only be accessed by authorized users. As projects evolve, access may need to be more relaxed to enable other stakeholders to access the data they need. Therefore, a Project may be edited to change users, teams, roles and entire permission schemes at any time. This makes it much easier to review and control access to your data.
Comprehensive Audit Logs
Onshape runs on a database in the cloud. Whenever you make a change to a design, it is instantly saved and replicated across multiple, geographically separated data centers in a matter of milliseconds. You never have to worry about losing data due to crashes, corrupt files or bad backups ever again.
These incremental saves enable Onshape Enterprise to track every interaction with your data in intricate detail. You can see who opened a Document, who made an edit and who exported or shared a Document, at what time and from what location. If somebody has touched your data in any way, their actions are recorded and logged forever and can be reviewed using Onshape Enterprise’s real-time Analytics and Reports.
Audit logs provide unprecedented transparency into how designs evolve and who has contributed to and/or accessed sensitive intellectual property. If somebody has accessed data they shouldn’t have or exported data without good reason, audit logs can be an indispensable tool for a forensic incident review, giving investigators crucial time-saving guidance to focus their inquiries.
Centralized Access Reports
Managers frequently need to review permissions to audit who currently has access to company data, when they previously had access and if they should still have access. Team members move from one project to another and contractors come and go, so being able to review data access in detail and make adjustments to permissions quickly is crucial.
Fortunately, this is very easy to do in Onshape Enterprise. Unlike old CAD and PDM systems, there are no local file copies to worry about and all access modifications are instant. Onshape Enterprise provides an up-to-the second view of intellectual property exposure and the power to make adjustments in tandem with inevitable changes to team composition and project lifecycles.
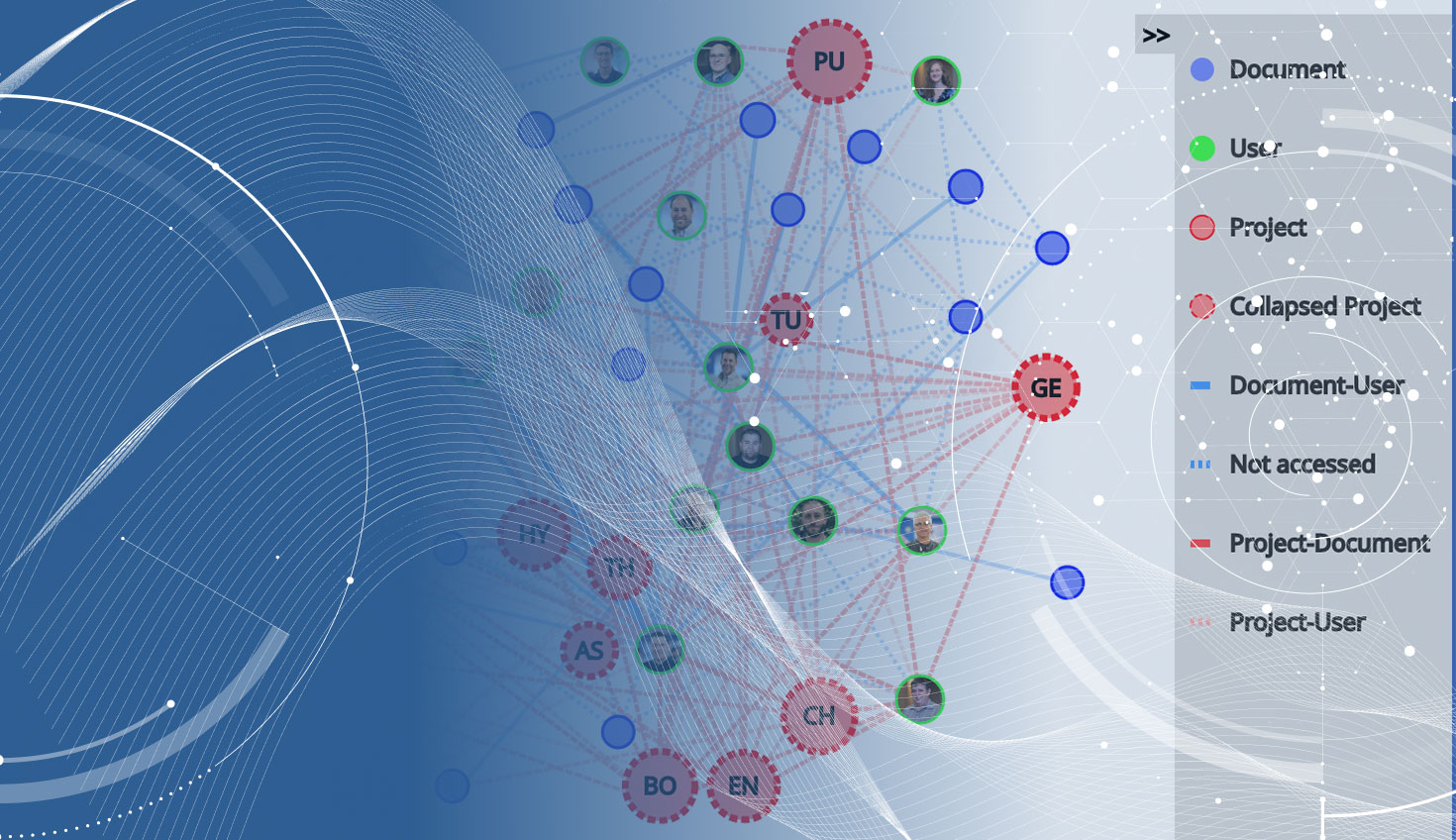
Document Access dependency graph showing access permissions to all company data.
The Document Access report is without a doubt the coolest looking chart in Onshape Enterprise, but don’t let the apparent complexity fool you. This chart enables you to drill down into each Project, Document and User to find out who has accessed a Project or Document, how much time they’ve spent on it and what their contributions have been. Powerful stuff and the type of insights that have never been possible before.
Enforced 2-Factor Authentication (2FA)
Onshape has always had the ability to add extra security using 2FA. This is an additional safeguard that can be used in case your login password has been compromised (which could be as simple as somebody looking over your shoulder as you log in). When 2FA is enabled, each user must enter a 6-digit code generated from a smartphone app like Google Authenticator. This code changes every 30 seconds, so even if somebody obtained your password and your 2FA code, they would only have a brief window in which to use it.
Onshape Enterprise can enforce a number of company-wide attributes including custom properties, materials databases, drawing templates and 2FA. By enforcing 2FA, Onshape Enterprise ensures that any person who wishes to access your company data has been challenged at least twice (password and 2FA code) and is a fully authenticated user.
Setting up 2FA with a QR code.
Secure Control With Onshape Enterprise
In last week’s blog, I posed the question: How do you keep your data secure, but allow easy access for anyone who needs it? The answer lies in Onshape Enterprise’s additional security features that not only make accessing data more secure, but also make it easier to track user activity and analyze access permissions across all of the data in your company.
If data security, analytics and ease of access are vital to your business – in addition to state-of-the-art 3D CAD and built-in data management with release workflows – Onshape Enterprise was created for you.